Sigbash Terms of Service (SaaS)
Version 1.0
Effective Date: 02/01/2026
These Terms of Service ("Terms") govern access to and use of the Sigbash hosted software and related documentation (collectively, the "Service") provided by Oblivia Incorporated ("Oblivia," "Provider," "we," "us"). These Terms are incorporated into and form part of any order form, quote, statement of work, or similar ordering document that references these Terms (each, an "Order") between Oblivia and the customer identified in the Order ("Customer," "you"). If there is a conflict between an Order and these Terms, the Order controls for that conflict.
1) Definitions
- "Affiliate" means an entity that controls, is controlled by, or is under common control with a party.
- "Authorized Users" means Customer's employees and Permitted Contractors authorized to use the Service under the applicable Order.
- "Customer Data" means data submitted to the Service by or on behalf of Customer, including policies, configurations, metadata, and other inputs, excluding Oblivia's Confidential Information.
- "Documentation" means user documentation Oblivia makes generally available for the Service.
- "Lightning Invoice" means a payment request over the Lightning Network (e.g., BOLT11 or successor format) issued by Oblivia or its payment processor for fees due under these Terms.
- "Permitted Contractors" means Customer's non-competing contractors who are bound by written confidentiality obligations at least as protective as these Terms.
- "Subscription Term" means the term stated in an Order (or if none, the period during which Customer is authorized to use the Service).
2) Subscription; License; Use Rights
2.1 Subscription grant
Subject to these Terms and the applicable Order, Oblivia grants Customer a limited, non-exclusive, non-transferable, revocable right during the Subscription Term to access and use the Service for Customer's internal business purposes and only as described in the Documentation.
2.2 Authorized Users; access controls
Customer may allow Authorized Users to access the Service. Customer is responsible for all use of the Service under its accounts, including all actions taken by Authorized Users and Permitted Contractors, and for maintaining the confidentiality and security of credentials, passkeys, PINs, recovery factors, API tokens, and other access mechanisms.
2.3 Subscription scope (Node / Server / Site)
Unless otherwise stated in the Order:
- Node-based means use is limited to the number of uniquely identified devices ("Nodes") specified in the Order.
- Server-based means use is limited to the number of servers specified in the Order.
- Site means use by an unlimited number of Authorized Users solely for Customer's internal benefit.
No subscription is a concurrent-user license unless expressly stated.
Customer may reassign Nodes as needed provided Customer does not exceed the licensed count.
2.4 Use restrictions
Customer will not, and will not permit any third party to:
- copy, modify, create derivative works of, decompile, disassemble, or reverse engineer the Service or any portion of it, or attempt to derive source code (except to the extent prohibited by applicable law);
- access the Service to build or improve a competing product or service;
- circumvent or disable security, rate limits, access controls, signing constraints, or usage restrictions;
- provide, resell, sublicense, time-share, or otherwise make the Service available to any third party, except as expressly permitted for Authorized Users in these Terms;
- use the Service to violate any law, regulation, third-party rights, or contractual obligation;
- upload or transmit malicious code (including malware, worms, time bombs, etc.);
- frame, mirror, syndicate, or replicate any portion of the Service or any Customer interface that provides access to the Service, except as expressly permitted in writing by Oblivia.
2.5 Reverse engineering (expanded)
For clarity, reverse engineering includes: converting object code to human-readable form; translating object code to source code (or approximations); studying behavior to recreate source code or internals; or any similar activity. If any such activity is permitted by law notwithstanding this restriction, results are Oblivia Confidential Information.
2.6 Customer Data license to Oblivia
Customer grants Oblivia a non-exclusive, worldwide, royalty-free license to host, process, transmit, display, and use Customer Data solely to provide, secure, maintain, and improve the Service and to perform any support services.
3) Fees; Taxes; Payment
3.1 Fees; Lightning invoicing at signing time; late payments; suspension
Fees (if any) will be as stated in the applicable Order or otherwise communicated in the Service.
Current status: fees are currently disabled. Oblivia may enable fees in the future upon notice through the Service, Documentation, an Order, or other written notice.
When fees are enabled, Customer agrees that:
- fees may be assessed per signing request, per policy, per account, per usage tier, or as otherwise stated in the Service or Order; and
- Oblivia may require payment via a Lightning Invoice presented at signing time (or immediately prior to completing a signing action).
If a Lightning Invoice is required, Oblivia may decline, pause, or fail a signing action until the invoice is paid. Customer is responsible for ensuring it can pay Lightning Invoices (including routing, liquidity, and invoice expiry constraints).
If Customer has an invoice-based plan (as stated in an Order), invoices are due net 30 days from invoice date. Late amounts accrue interest at 1.5% per month (or the maximum allowed by law, if lower) plus reasonable collection costs.
Oblivia may suspend access for delinquent payments 15 days past due (except for amounts under good-faith dispute where the parties are actively working to resolve the dispute).
Invoice disputes must be submitted in writing within 30 days of invoice date.
3.2 Taxes
Fees are exclusive of taxes. Customer is responsible for all applicable sales, use, VAT, excise, import duties, and similar taxes (excluding Oblivia's income taxes). If withholding is required by law, Customer will gross up payments so Oblivia receives the amount it would have received absent withholding, and Customer will provide appropriate receipts.
4) Hosting; Support; Service Levels
4.1 Availability
Oblivia will use commercially reasonable efforts to make the Service available. Any service levels, if offered, must be stated in an Order or an SLA addendum.
4.2 Support
If support is purchased, Oblivia will provide support in accordance with the Order (and any applicable support policy).
4.3 Remedies
If Oblivia fails to perform paid support services materially as described, Customer's exclusive remedy is: (a) Oblivia will use commercially reasonable efforts to correct the issue within 30 days after written notice; and (b) if not corrected, Oblivia will refund the fees paid for the non-conforming support services.
5) Ownership; Marks; Publicity
5.1 Oblivia ownership
Oblivia (and its licensors) retain all right, title, and interest in and to the Service, Documentation, and all related technology, including improvements and derivatives. No rights are granted except as expressly stated.
5.2 Customer ownership
Customer retains all right, title, and interest in Customer Data.
5.3 Marks; publicity permission (default on)
Each party retains ownership of its trademarks, service marks, and logos ("Marks"). Customer grants Oblivia permission to use Customer's name and Marks in Oblivia's customer lists, website, presentations, press releases, case studies, social media, and other marketing materials, provided Oblivia uses Customer's Marks in a manner consistent with any written brand guidelines provided by Customer.
Customer may revoke this permission at any time by written notice, and Oblivia will stop using Customer's Marks in new materials within a commercially reasonable time (and may continue to use previously published materials until updated in the ordinary course).
6) Confidentiality; Privacy
6.1 Confidential Information
"Confidential Information" means non-public information disclosed by a party that is designated confidential or that reasonably should be understood as confidential given the nature of the information and the circumstances. Oblivia's Confidential Information includes the Service (including its design and security architecture), non-public Documentation, and these Terms.
6.2 Obligations
The receiving party will: (a) use Confidential Information only to perform under these Terms; (b) protect it using reasonable care (at least the same as it uses for its own similarly sensitive information); and (c) disclose it only to employees and contractors with a need to know who are bound by confidentiality obligations at least as protective as these Terms.
6.3 Exclusions
Confidentiality obligations do not apply to information that: (i) becomes public without breach; (ii) was independently developed without use of the other party's Confidential Information; (iii) is rightfully obtained from a third party without duty of confidentiality; or (iv) was already known without obligation of confidentiality.
6.4 Compelled disclosure
A party may disclose Confidential Information to comply with law or valid legal process if it gives prompt notice (if legally permitted) and cooperates in seeking protective treatment.
6.5 Privacy and account information
Oblivia may access, use, and disclose information about Customer accounts and Authorized Users to: (a) provide and secure the Service; (b) comply with law and legal process; (c) enforce these Terms; and (d) protect rights, safety, and property.
7) Security; Digital Assets; Customer Responsibilities (Sigbash-specific)
7.1 No custody; no transfer of title; no fiduciary role
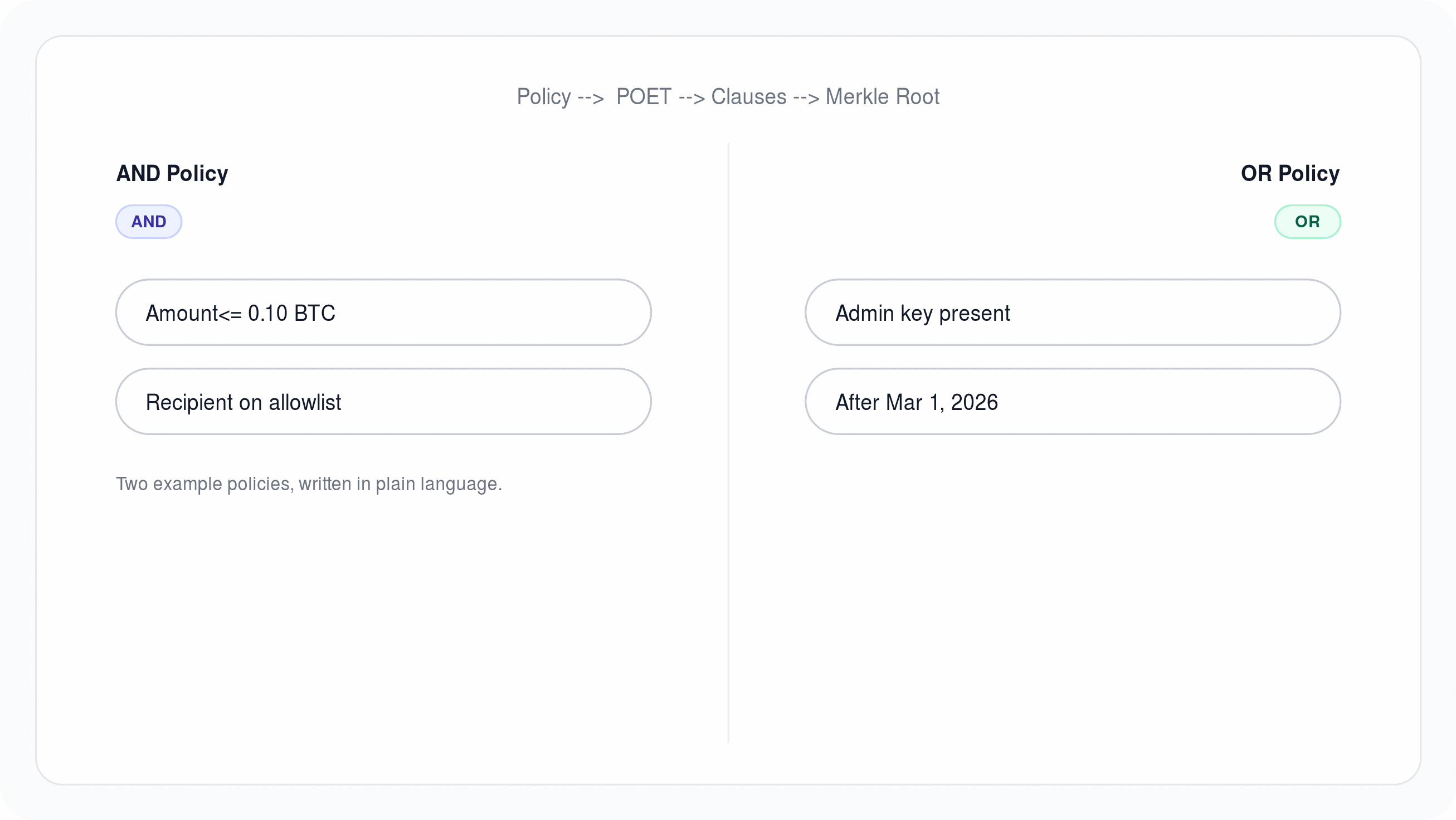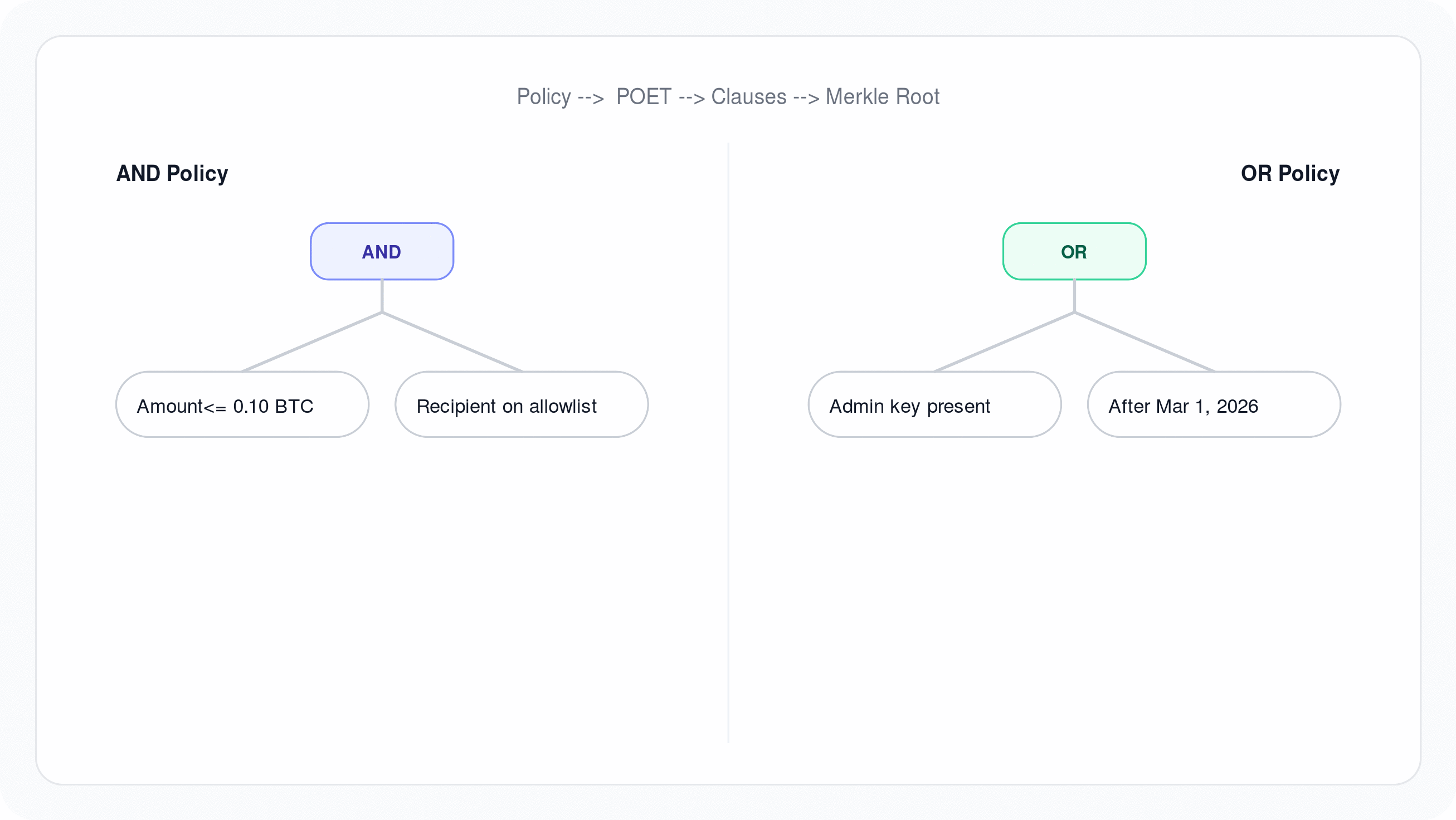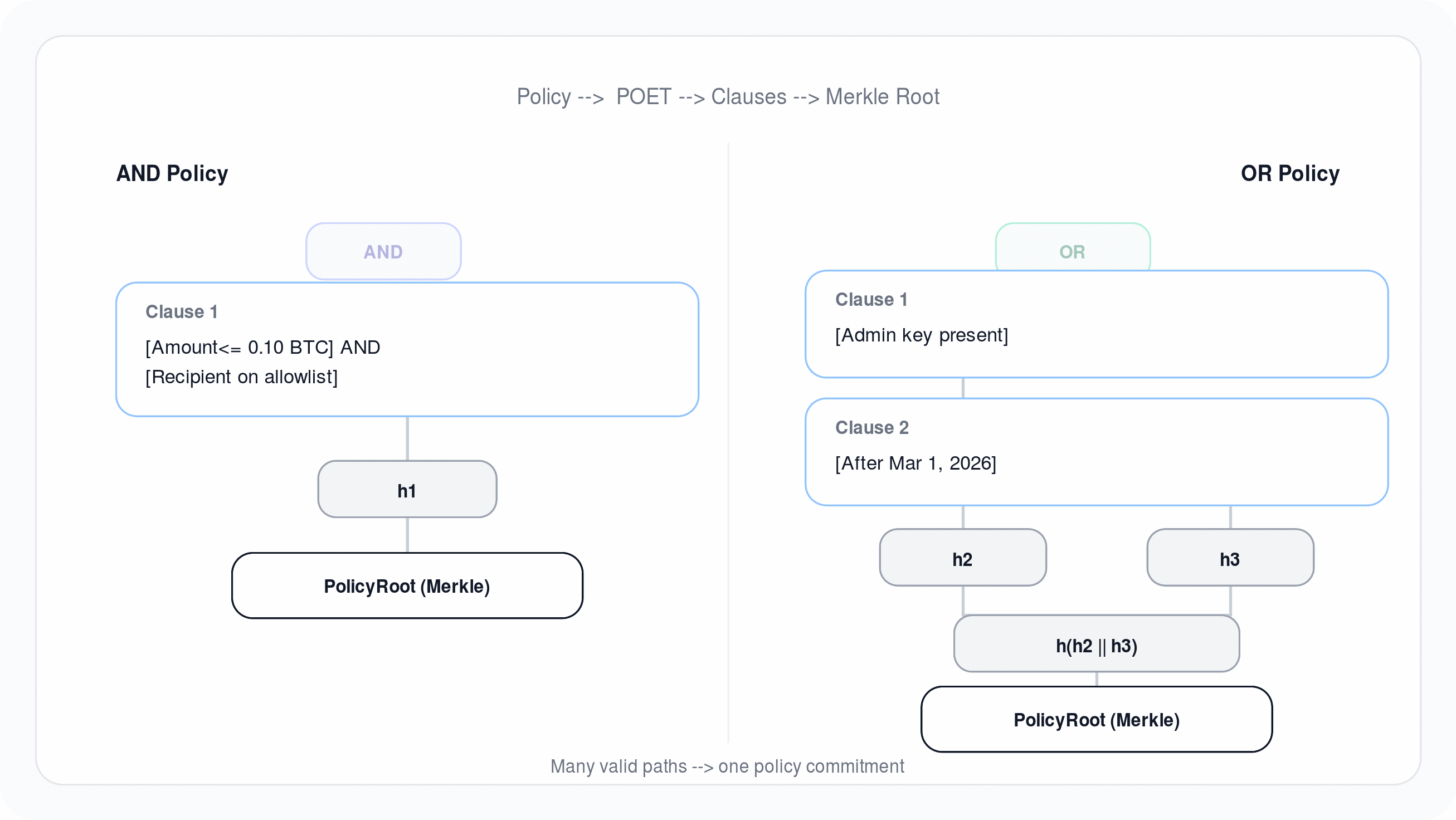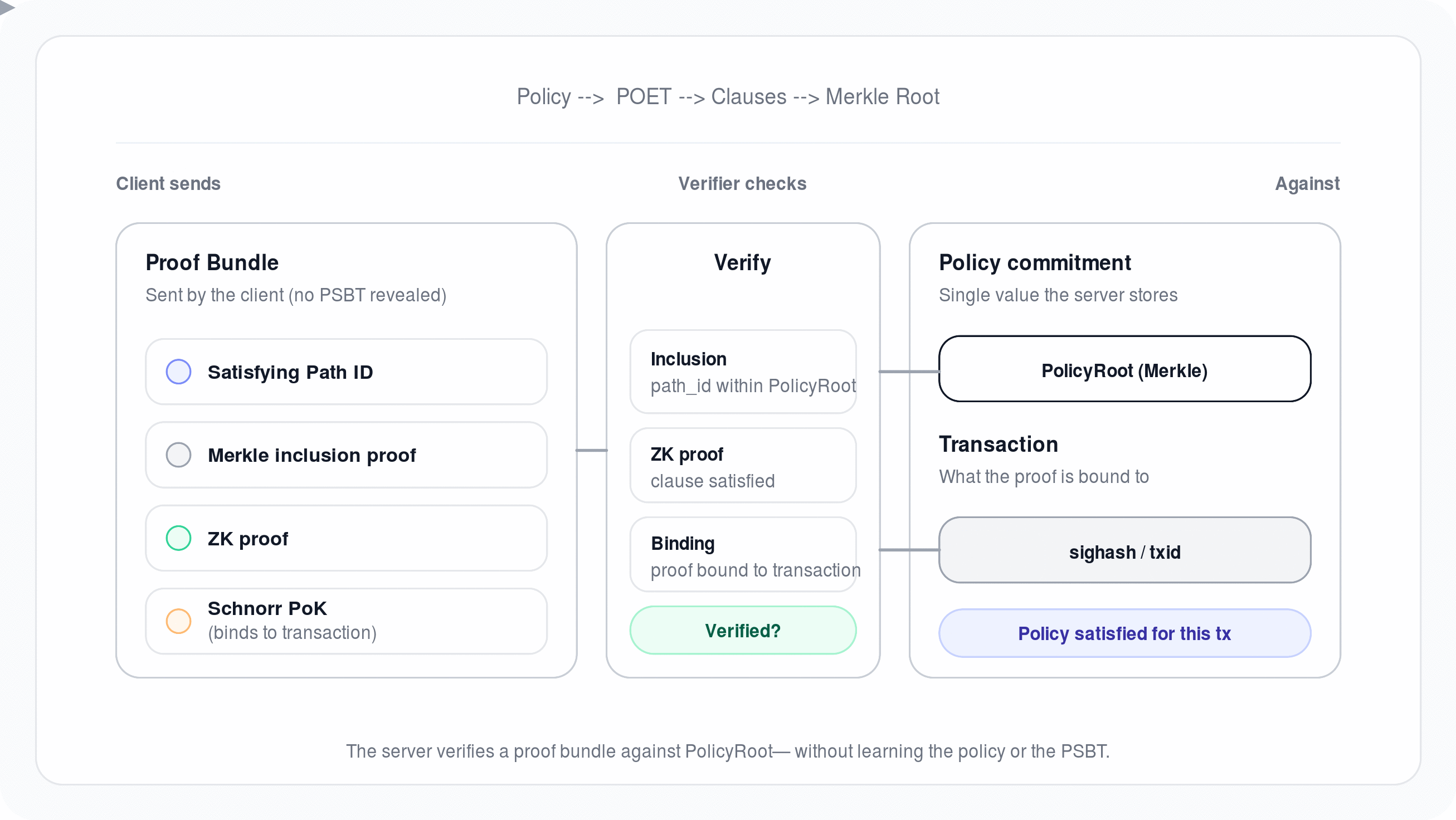
Customer acknowledges that Sigbash may be used in workflows involving digital assets, wallets, signing policies, and transaction authorization.
Oblivia does not take custody of Customer's digital assets, does not hold Customer funds as a custodian, does not act as a broker, dealer, financial advisor, escrow agent, or fiduciary, and does not guarantee that any transaction is safe, appropriate, profitable, or compliant. Title to and control over Customer's digital assets remain solely with Customer and its wallet software, key holders, and operational processes.
7.2 Customer responsibility for keys, policies, and transactions
Customer is solely responsible for:
- verifying the correctness and suitability of any policies, rules, templates, and configurations it creates or uploads;
- validating any transaction data it submits or authorizes for signing;
- maintaining secure custody practices for wallets, keys, passkeys, recovery materials, and access factors not explicitly managed by Oblivia; and
- ensuring Authorized Users are trained, authorized, and acting within Customer's internal controls.
Oblivia does not control the economic outcome of any transaction and does not guarantee that the Service will detect every malicious or unsafe transaction pattern.
7.3 Emergency security actions; incident response boundaries
Customer acknowledges that security incidents, attacks, abuse, and abnormal signing patterns may occur. To protect the Service, customers, and third parties, Oblivia may take reasonable emergency actions including (without limitation) suspending or throttling accounts, denying signing requests, invalidating sessions, rotating keys or credentials under Oblivia's control, modifying rate limits, or temporarily disabling features ("Emergency Actions").
Oblivia will use commercially reasonable efforts to (a) notify Customer of Emergency Actions when practicable, and (b) restore access once the underlying risk is mitigated. Emergency Actions taken in good faith will not be deemed a breach of these Terms.
7.4 Prohibited high-risk or unlawful use
Customer will not use the Service in violation of sanctions, anti-money laundering laws, or other applicable financial crime regulations, or for any unlawful purpose.
8) Warranties; Disclaimers
8.1 No malicious code
To Oblivia's knowledge, the Service does not contain intentionally malicious code designed to damage systems or exfiltrate data. Customer must promptly notify Oblivia of suspected nonconformance and reasonably cooperate in investigation and remediation.
8.2 Authority
Each party represents it has the power and authority to enter into these Terms and that Orders will be executed by an authorized representative.
8.3 Professional services
If Oblivia performs paid services, Oblivia will perform them in a professional and workmanlike manner.
8.4 Disclaimer
EXCEPT AS EXPRESSLY STATED IN THESE TERMS, THE SERVICE AND ALL RELATED MATERIALS ARE PROVIDED "AS IS" AND "AS AVAILABLE." OBLIVIA DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT, AND ANY WARRANTY THAT THE SERVICE WILL BE UNINTERRUPTED, ERROR-FREE, OR SECURE. CUSTOMER ACKNOWLEDGES THAT INTERNET CONNECTIVITY, LIGHTNING PAYMENTS, AND THIRD-PARTY SYSTEMS CREATE RISKS OF OUTAGES, FAILED PAYMENTS, AND DATA LOSS.
8.5 Modifications void warranties
Any warranties are void to the extent failures are caused by Customer's modifications, misuse, or use outside the permitted scope.
9) Indemnification
9.1 Oblivia IP indemnity
Oblivia will defend Customer against third-party claims that the Service, as provided by Oblivia, infringes a U.S. patent, copyright, or trade secret, and will pay damages finally awarded (or approved settlements), provided Customer: (a) promptly notifies Oblivia; (b) gives Oblivia sole control of defense and settlement; and (c) reasonably cooperates.
Oblivia has no obligation for claims arising from: (i) modifications not made by Oblivia; (ii) combination with Customer or third-party systems where the claim would not exist otherwise; or (iii) use outside the permitted scope.
If infringement is alleged, Oblivia may: (a) procure the right to continue; (b) modify or replace; or (c) terminate the affected portion and refund prepaid fees for the terminated portion covering the prior 12 months (or the unused prepaid portion, if applicable).
9.2 Customer indemnity
Customer will defend and indemnify Oblivia and its officers, directors, employees, contractors, and agents against third-party claims arising from: (a) Customer Data; (b) Customer's use of the Service in violation of these Terms or law; (c) Customer's gross negligence or willful misconduct; or (d) Customer's violation of third-party rights or third-party terms.
9.3 Indemnification procedure
The indemnified party must provide prompt notice and reasonable cooperation. The indemnifying party controls defense and settlement, but may not settle in a way that admits fault or imposes non-monetary obligations on the indemnified party without consent.
10) Limitation of Liability
10.1 Liability cap (indemnities excluded)
TO THE MAXIMUM EXTENT PERMITTED BY LAW, EXCEPT FOR: (A) CUSTOMER'S PAYMENT OBLIGATIONS, (B) CUSTOMER'S BREACH OF SECTION 2 (USE RESTRICTIONS), AND (C) A PARTY'S INDEMNIFICATION OBLIGATIONS UNDER SECTION 9, EACH PARTY'S TOTAL LIABILITY ARISING OUT OF OR RELATED TO THE TERMS WILL NOT EXCEED THE AMOUNT PAID BY CUSTOMER TO OBLIVIA IN THE 12 MONTHS PRECEDING THE EVENT GIVING RISE TO THE CLAIM.
10.2 Exclusion of consequential damages
TO THE MAXIMUM EXTENT PERMITTED BY LAW, NEITHER PARTY WILL BE LIABLE FOR INDIRECT, INCIDENTAL, SPECIAL, CONSEQUENTIAL, EXEMPLARY, OR PUNITIVE DAMAGES, OR FOR LOST PROFITS, LOST REVENUE, BUSINESS INTERRUPTION, OR LOSS OF GOODWILL, EVEN IF ADVISED OF THE POSSIBILITY.
11) Term; Termination
11.1 Term; renewal
These Terms remain effective until all Orders expire or are terminated. Each Order renews as stated in the Order. If not stated, Orders auto-renew for the same term unless either party gives written notice of non-renewal at least 60 days before the end of the then-current term.
11.2 Termination by Oblivia
Oblivia may terminate an Order (or suspend access) if:
- Customer fails to pay undisputed fees within 15 days of due date (or fails to pay required Lightning Invoices at signing time when fees are enabled);
- Customer materially breaches and fails to cure within 30 days after written notice; or
- Customer becomes insolvent, files for bankruptcy, or similar events occur.
11.3 Termination by Customer
Customer may terminate an Order if Oblivia materially breaches and fails to cure within 90 days after written notice (or a longer period if Oblivia is diligently working toward a cure).
11.4 Effect of termination
Upon termination or expiration, Customer's right to access the Service stops, and Customer will not attempt to bypass access controls. Upon request, Oblivia will make Customer Data available for export for a limited period, if technically feasible and commercially reasonable (and subject to legal/security constraints).
11.5 Accrued rights
Termination does not affect accrued payment obligations or either party's right to seek remedies.
12) Feedback; Usage Analytics
Customer grants Oblivia a perpetual, irrevocable, worldwide, royalty-free right to use and incorporate feedback, suggestions, and improvement ideas without restriction or obligation. Oblivia may collect and use aggregated and anonymized usage analytics to operate, improve, and market the Service, provided such analytics do not identify Customer or include Customer Confidential Information.
13) Miscellaneous
13.1 Assignment
Customer may not assign these Terms without Oblivia's prior written consent (not unreasonably withheld). Oblivia may assign these Terms in connection with a merger, acquisition, reorganization, or sale of substantially all assets, or to an Affiliate.
13.2 Subcontractors
Oblivia may use subcontractors to provide the Service, provided Oblivia remains responsible for performance and ensures subcontractors are bound by appropriate confidentiality obligations.
13.3 Compliance with laws
Each party will comply with applicable laws and regulations.
13.4 Force majeure
Neither party is liable for delays or failures due to events beyond its reasonable control.
13.5 Government restricted rights
If the Service is used by or for the U.S. Government, it is provided with restricted rights as applicable under federal regulations.
13.6 Notices
Notices must be in writing and delivered to the addresses in the Order (or as later updated in writing). Notices of breach must describe the breach with reasonable detail.
13.7 Non-solicitation (optional)
During the term and for 2 years after, Customer will not solicit for hire Oblivia personnel involved in delivering the Service. (Any liquidated damages for breach must be explicitly stated in the Order or an addendum.)
13.8 Severability; waiver
If any provision is unenforceable, it will be modified to the minimum extent necessary and the remainder remains in effect. Failure to enforce is not a waiver.
13.9 Entire agreement; order of precedence
These Terms and the Orders are the entire agreement and supersede prior discussions. Conflicting PO/invoice terms are void.
13.10 Governing law; venue; dispute resolution
These Terms are governed by the laws of the State of Delaware, excluding its conflict-of-laws rules, and excluding UCITA and CISG to the maximum extent permitted.
Exclusive venue for disputes is state or federal courts located in Delaware, and each party consents to personal jurisdiction there.
Before filing suit (except for injunctive relief), the parties will attempt good-faith executive escalation and mediation. Customer must provide Oblivia a reasonable opportunity to cure alleged breaches with a written notice describing the breach in reasonable detail and a 30-day cure period (or longer if Oblivia is diligently working toward cure).